Optimizing Container Image Pull Efficiency: A Technical Deep Dive
For cloud-based containerized application deployment and management, Amazon ECS and Amazon ECR are essential. ECR provides a secure Docker registry for managing and storing container images, while ECS coordinates the deployment of Docker containers on AWS Fargate or Amazon EC2 instances. To run containers effectively, developers push Docker images to ECR, which ECS then pulls.
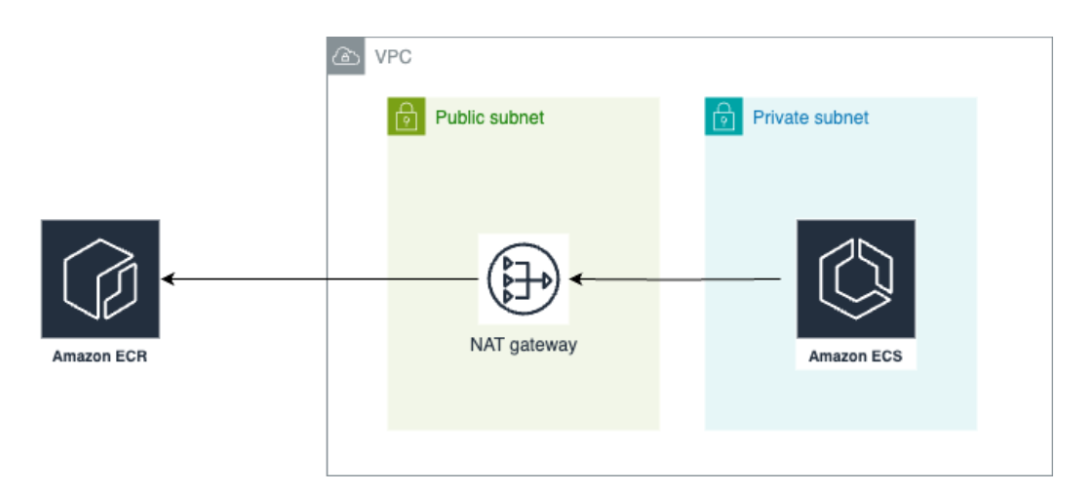
ECS tasks are typically executed within a Virtual Private Cloud (VPC) private subnet, which is separated from the public internet for added security. ECS tasks use a NAT gateway in a public subnet to retrieve images from ECR. This keeps the tasks safe from incoming internet traffic while enabling secure access to ECR.
Problem Statement
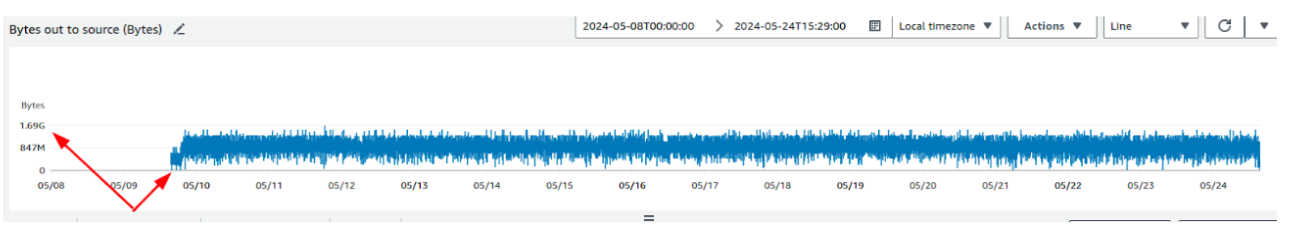
On a routine Monday morning, a critical alert disrupted our normal workflow: “AWS Bill Alert: Unusual Activity Detected.” The sudden spike in cloud costs pointed to excessive data transfer through the NAT Gateway. Upon investigation, the culprit was an ECS service that repeatedly spun up and terminated containers due to health check failures. Each container restart required pulling an image from ECR, increasing costs due to data transfer through the NAT Gateway.
The Hidden Costs
While AWS advertises that pulling images from ECR within the same region is free, this refers to the ECR service itself. The network traffic via the NAT Gateway is still billable. Each gigabyte of data transferred through a NAT Gateway incurs costs, which add up quickly with frequent container restarts.
- NAT Gateway Pricing: $0.045 per GB of data transferred through the NAT Gateway Source: AWS VPC Pricing.
Frequent container restarts, especially with large Docker images, further amplified the costs.
Technical Deep Dive: Why Costs Escalate
When ECS tasks frequently terminate and restart, they pull Docker images from ECR repeatedly. Even though AWS provides free data transfer within the same region for ECR, the NAT Gateway traffic incurs charges, as noted in the AWS blog on Understanding Data Transfer Costs for AWS Container Services.
Each image pulled through the NAT Gateway triggers billable data transfers, leading to significant increases in cloud costs, particularly in unstable services with frequent restarts.
Strategies for Optimization
- Monitoring NAT Gateway Usage
-
- Use AWS CloudWatch to monitor NAT Gateway traffic. Set up alarms for spikes in data transfer. For details, visit the AWS CloudWatch Documentation.
- Leverage AWS Cost Explorer to track cost trends and detect anomalies in NAT Gateway expenses.
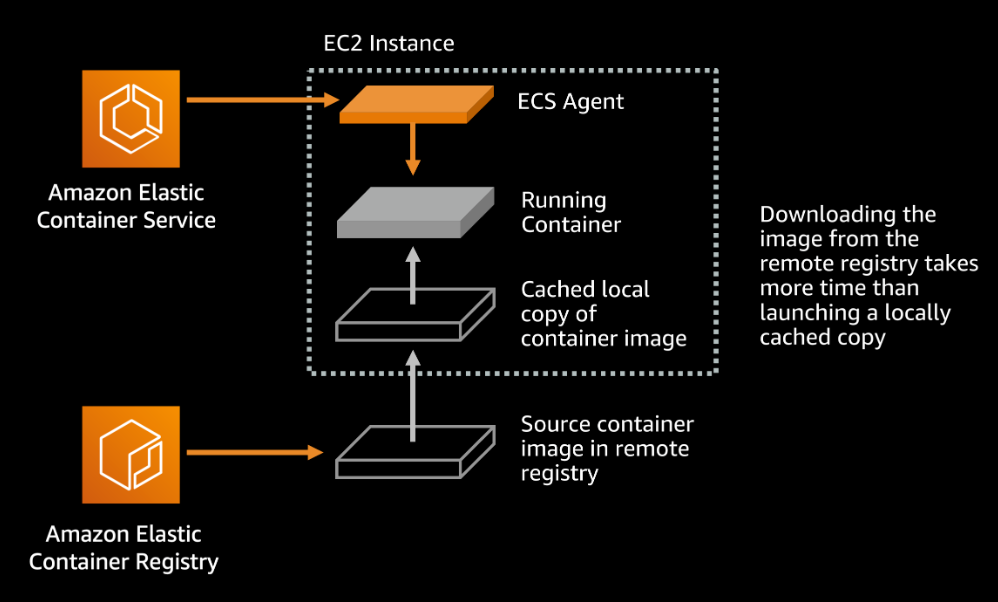
2. Local Image Caching (only for ECS running on EC2)
Steps to Set Up Local Image Caching:
2.1. Configure the ECS Task to Use EC2 Launch Type:
-
-
-
- Ensure that your ECS service is using the EC2 launch type (not Fargate), as local caching can be configured directly on EC2 instances running ECS tasks.
-
-
2.2. Pre-Pull Images with an EC2 Bootstrap Script:
-
-
-
- You can set up a bootstrap script on your EC2 instances to pull the required Docker images when the instance is launched. This way, the image will be pre-cached on the instance and ready for use by ECS tasks.
-
-
#!/bin/bash
IMAGE_NAME="your-repository/your-image:tag"
# Check if the image is already cached
if [ ! "$(docker images -q $IMAGE_NAME 2> /dev/null)" ];
then
echo "Image not found in local cache. Pulling from ECR..."
docker pull $IMAGE_NAME
else
echo "Image already cached locally." fi2.3. Create the EC2 AMI with Pre-Pulled Images:
-
-
-
- Use EC2 Image Builder or manually create a custom AMI with the required images pre-pulled.
-
-
Implement local image caching to reduce the frequency of image pulls from ECR.
3. Enhancing ECS Fargate Stability
-
-
- Enable deploymentCircuitBreaker to halt unhealthy deployments and set rollback=true to automatically revert to stable deployments if issues occur AWS ECS Circuit Breaker Blog.
- When you enable the deploymentCircuitBreaker in ECS, it monitors the health status of ECS tasks during the deployment process. If the deployment encounters issues (e.g., failing health checks or misconfigurations), the circuit breaker interrupts the deployment process, preventing further rollouts of the problematic version.
-
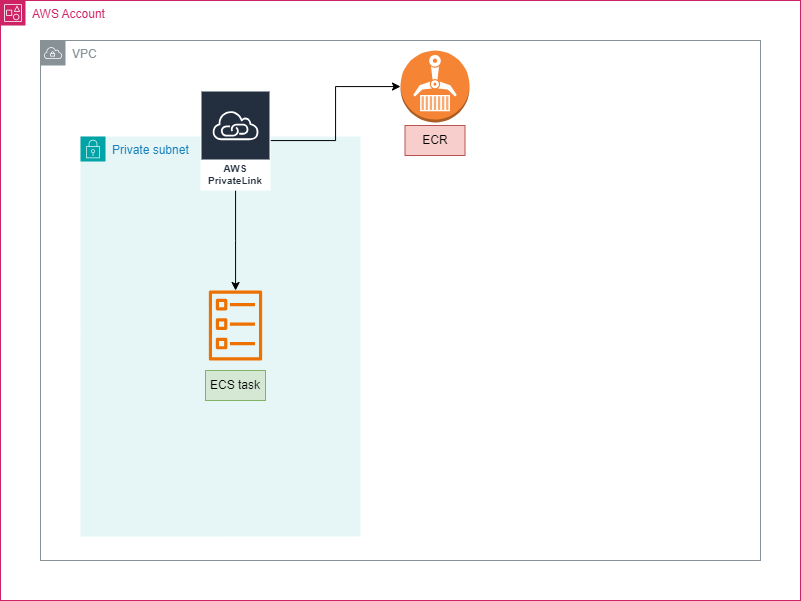
4. AWS PrivateLink
-
-
- Implementing AWS PrivateLink for ECR Using AWS PrivateLink enables private, secure communication between ECS tasks and ECR without using a NAT Gateway, reducing costs.
PrivateLink charges $0.01 per GB for data transfer within the AWS network AWS PrivateLink Pricing.
- Implementing AWS PrivateLink for ECR Using AWS PrivateLink enables private, secure communication between ECS tasks and ECR without using a NAT Gateway, reducing costs.
-
Cost comparison for 40 TB data transfer:
-
-
- NAT Gateway: ~$1,800/month.
- PrivateLink: ~$400/month.
-
Note: In case we have a fixed cost of $7.3 per month per AZ in a region.
Calculation → $0.01/hour * 730/month = $7.3
Note: This price is for the region ‘Ohio’, price may vary from region to region.
Above estimation is for 3 AZ’s
Conclusion
This whole experience taught me a valuable lesson: in the world of cloud, what seems free at first glance can often hide sneaky costs. It’s like those “free” samples at the grocery store – sure, the bite-sized morsel is free, but before you know it, you’ve bought the whole package.
Optimizing container image pull efficiency can significantly reduce costs, particularly by managing NAT Gateway traffic. By implementing caching mechanisms, using AWS PrivateLink, optimizing task configurations, and stabilizing ECS services, teams can ensure cost-efficient and resilient ECS deployments.