9 Security Best Practices in Identity and Access Management
In this blog, we will be covering Cloud Provider’s service called Identity and Access Management (IAM). It is essential that organizations ensure their IAM users, roles, and policies/permissions are implemented according to updated security policies.
IAM is a formation of policies and technologies to ensure that the users have the right access to the technology resources. We will be covering the security best practices for key components of IAM:
- Users – Human users, aka Human Identities, could be internal or external users
- Roles – Set of policies utilized to access resources by users or cloud services
- Policies – Set of permissions to access cloud services
This blog will help you by providing information on how to start implementing IAM within your organization, while cloud native applications development and incorporating IAM best practices into your security strategy. We will achieve:
- Improved employee engagement & productivity
- Enhanced Security
- Reduced IT Costs
- Maintain Compliance
Downloads
Article (PDF-276 KB)MOST POPULAR INSIGHTS
- Optimizing Container Image Pull Efficiency: A Technical Deep Dive
- Streamline Your Application Delivery with AWS AppStream 2.0: An Introduction
- Secure Communication in a Hybrid Cloud – A Case of Site-to-Site VPN on AWS
- Understanding, Communicating and Making Informed Decisions with Data Visualization
- Cross-Account, Cross-Region Backups in AWS
Best Practices
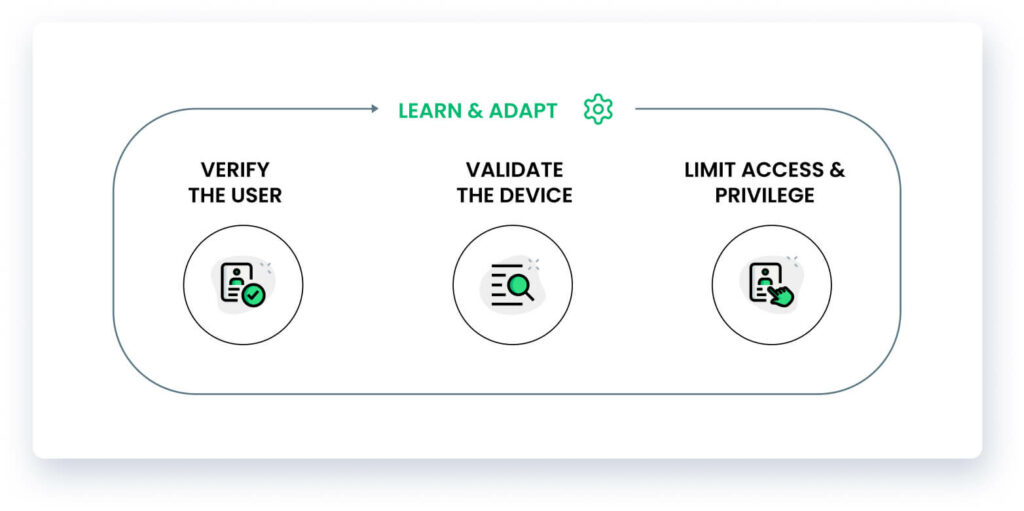
To start the journey of security, one must understand what the zero trust security model is.
1. Zero Trust Approach to Security
Core principles for a Zero Trust security model are:
- Never trust
- Always verify
- Assume breach
- Apply for least-privileged access
The Zero Trust approach & IAM tools work well together. The essential rule of the Zero Trust approach is giving least-privileged access while utilizing IAM tools to simplify and streamline the validation process to allow the right access without interrupting workflows.
No matter how much security you implement, enforcing a strong password policy is the first key to security.
2. Strong Password Policy
If your team is utilizing Single Sign-On (SSO) tools, it’s vital that each user’s password is difficult to guess, unique, and strong password. Strong passwords always act as the first line of defense against cyberattacks such as DDOS or brute force. Make sure passwords are frequently updated and not reused.
Once the password is secured, it’s essential to implement Multiple Factor Authentication (MFA) as an added layer of security.
3. Enforce MFA
To protect root & IAM users, we must leverage the advantage MFA brings. It’s always recommended that you use a USB Security Key, dependent on the key’s presence and the owner’s fingerprint scanning. Alternatively, there are authentication tools like Google Authenticator which can fulfill the purpose as well. Until and unless both password and correct key parameters are inserted, users cannot access the services.
A user with all privileges is called a root user, and it must be secured.
4. Protecting the root user
It’s advised by all the cloud providers never to use the root user for day-to-day operations. Root privileges should only be used when there’s no alternate available. We should always avoid generating access keys for root accounts because things can go south pretty quickly in the event they get leaked or if they are left somewhere lurking in the machine and are later discovered by a malicious actor.
When you open your doors for external users, an extra layer of protection should be implemented by using Identity Providers.
5. Identity Providers for users with Temporary Credentials
Human users can also be external users that we are collaborating with and require access to the cloud resources. This can be done using a mobile app, custom application, web browser, or interactive command-line tools. Identity Providers like Active Directory or Google Workspace can be utilized for external/internal human users to provide federated access with temporary credentials. Set up SSO, LDAP for AD, or Federated access to achieve best practices.
In cases where you require long-term credentials, utilize access keys and make sure they are regularly rotated.
6. Regular access key rotations
Regularly rotating long-term credentials help you familiarize yourself with the process. This is useful in cases where you must rotate credentials, such as when an employee leaves your company, their access keys are still active. Information such as the ‘last used’ of access keys gives you better insights.
The best practice for assigning roles & permissions is to ensure that least-privilege permissions are granted to users.
7. Least-privilege permissions
It is crucial to limit excessive permissions to admin to ensure single admins don’t have excessive control. Divide responsibilities among people to avoid over-provisioning access and embrace Privileged Access Management (PAM) best practices. However, the goal is to perform regular audits and make corrections where unnecessary standing permissions are identified.
When we have already protected our users, roles & policies, we need to make sure processes are followed in a clockwork manner. Automating workflows can help us achieve this.
8. Automate workflows
Automation streamlines the workflows, reduces manual errors, and supports governance and compliance needs. It also helps in logging, auditing, and generating reports at regular intervals for compliance requirements.
Even with the strong policies and processes of IAM, over-provisioning remains a problem. Regular audits help in rectifying those issues.
9. Regular Audit
We already agreed that limiting access is one of the IAM security best practices, but it can only be achieved by consistently tracking what access users really need. By auditing usage logs and access permissions regularly, organizations can de-provision access and reduce their attack surface. They can also make sure audit schedules are strictly followed by people since it is dependent on human intervention.
Conclusion
The IAM domain is constantly evolving, but some essential IAM best practices can support any growing organization, ensuring IAM strategies are updated as they grow. These best practices will help you build an IAM framework and additionally strengthen your virtual asset security.
This series of blogs will continue to provide more details on how to implement above mentioned best practices into your cloud providers such as AWS, GCP, or Azure.
About The Author(s)
AUTHOR(S)

Established in 2012, Xgrid has a history of delivering a wide range of intelligent and secure cloud infrastructure, user interface and user experience solutions. Our strength lies in our team and its ability to deliver end-to-end solutions using cutting edge technologies.
OFFICE ADDRESS
US Address:
Plug and Play Tech Center, 440 N Wolfe Rd, Sunnyvale, CA 94085
Pakistan Address:
Xgrid Solutions (Private) Limited, Bldg 96, GCC-11, Civic Center, Gulberg Greens, Islamabad
Xgrid Solutions (Pvt) Ltd, Daftarkhwan (One), Building #254/1, Sector G, Phase 5, DHA, Lahore




